Playing Nice
Fortunately, there do exist solutions to the issues described in the previous section. Here we summarize some of the information available Globus Toolkit Firewall Requirements.First, we need to distinguish between two versions of the Globus Toolkit. Version 2 (GT2) has been around for several years and is used in a number of production Grids today. Version 3 (GT3) is based on industry standard Web services technologies and the Open Grid Services Infrastructure (OGSI) standards. GT4 was released in 2005 and is the latest version of the Globus software. While these versions are similar architecturally (both have GRAM, MDS, GridFTP), their network traffic characteristics differ.
For the three basic services, GRAM, MDS, and GridFTP, Table 1 describes the network ports that these services use and need to be allowed into a site in order to give users access to those services.
| Service | GT2 | GT3 | GT4 |
|---|---|---|---|
| GRAM | 2119 (1,2) | 8080 (2) | 8443 (2) |
| MDS | 2135 | 8080 | 8443 |
| GridFTP | 2811 (1,2) | 2811 (1,2) | 2811 (1,2) |
| All ports are TCP ports. (1) Additional ports are dynamically assigned by the created user processes. (2) Application is sensitive to NAT translation. |
|||
In addition to these services, the Job Manager and GridFTP request that a range of ports in the untrusted ephemeral range (port numbers greater than 1024) be open. If the firewall blocks ports in this range (many don't), then a range must be opened, and the environment variable GLOBUS_TCP_PORT_RANGE must be set so that all ports dynamically assigned by Globus Toolkit services fall into the opened range. The exact size of the opened range will depend on the exact usage of the system, but a good rule of thumb is ten ports per simultaneous user. Note that in GT3, the Job Manager uses the same port (default 8080) as the GRAM server, so the ephemeral port range is required only for the GridFTP service.
A Client Behind a Firewall
A user behind a firewall can use GT. In order to permit this, the firewall needs to allow a port range for callback connections from the GRAM service. This range should be opened as described in the previous section and the GLOBUS_TCP_PORT_RANGE variable set in the user's environment.If the user is behind a firewall doing NAT, the user will also need to set the environment variable GLOBUS_HOSTNAME to the external address of the firewall and configure the firewall to pass incoming connections in the port range specified by GLOBUS_TCP_PORT_RANGE through to his computer.
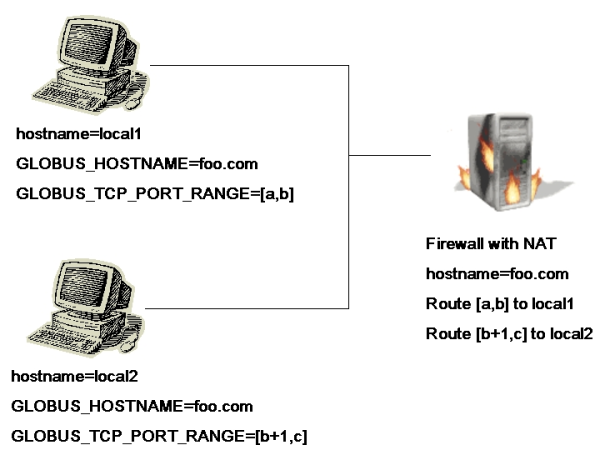
Most NAT devices are capable of translating the port numbers as well. Currently, however, GT does not have this capability, and therefore the port number on the internal machine on which a particular service is listening must be the same as on the external interface of the firewall. Thus, in the case of multiple machines behind a single NAT device, each machine must have a unique port range defined, and those ports must be forwarded to the appropriate machine by the firewall. (GLOBUS_HOSTNAME will be the same for all the machines, however.)
Future Directions
We hope that the leveraging of Web services protocols will enable firewalls that more intelligently allow traffic and relieve users of having to administer them manually. For example, with traffic being carried in self-describing, digitally signed XML messages, a router can easily parse and check the signature that authenticates the sender and open ports based on the result of such a validation.This work was supported in part by the Mathematical, Information, and Computational Sciences Division subprogram of the Office of Advanced Scientific Computing Research, Office of Science, U.S. Department of Energy, under Contract W-31-109-ENG-38 and under Contract DE-AC03-76SF0098 with the University of California; by the National Science Foundation; by the NASA Information Power Grid program; and by IBM.
Information in this article was developed through the DOE Science Grid.
Globus Toolkit is a registered trademark held by the University of Chicago.
| Sidebar One: Grid Resources |
|
A Brief Taxonomy of Firewalls /Great Walls of Fire, SAMS Institute, 2002 (pdf) Implementing Production Grids for Science and Engineering: W. Johnston et al.,in The Grid: Blueprint for a New Computing Infrastructure (Second Edition), ed. Foster and Kesselman, 2003 |
This article was originally published in ClusterWorld Magazine. It has been updated and formatted for the web. If you want to read more about HPC clusters and Linux you may wish to visit Linux Magazine.
Von Welch is a security researcher at the National Center for Supercomputing Applications where he works on Grid Security and contributes to the Globus Toolkit security architecture.
Olle Mulmo is an applications expert at the Swedish Royal Institute for Technology, where he works on Grid Security in national, Nordic, and European research and development projects and contributes to the Globus Toolkit architecture.


